Critical Infrastructure Security Showdown (CISS) 2024

Critical Infrastructure Security Showdown 2023 (CISS 2023) is a premier and one-of-its-kind cyber exercise in operational technology. This international exercise is held entirely remotely and opened to invited international participants. CISS 2023 is a organized by iTrust (Centre for Research in Cyber Security), sponsored by the Cyber Security Agency of Singapore and co-organised with the Ministry of Defence, Singapore.

iTrust is the proud host of several world-class testbeds and training platforms. These testbeds and training platforms together constitute a one-of-a kind facility for research and training in the design of safe and secure large-scale cyber-physical systems. The interconnected testbeds support R&D, technology validation, international cyber exercises, education and training programmes towards the safety and security of cyber-physical systems.
The objectives of CISS 2023 was to develop capabilities for defending critical infrastructure (CI) / cyber-physical systems (CPS) under cyber-attacks, validate and assess the effectiveness of technologies developed by researchers & commercial entities with iTrust, understand composite Tactics, Techniques and Procedures (TTPs) for enhanced Operation Security.
CISS 2023 marked my first exposure to Operational Technologies (OT), a field that captivated my interest due to its intricate connection with critical infrastructures. Its distinct characteristics set it apart from Informational Technologies (IT), and the consequences of exploitation are beyond comprehension.
This marks my second OT-themed CTF, following my first participation in CISS 2023. To prepare for this competition, I purchased a PLC and developed a proof-of-concept actuator and sensor to train and equip my team at Ensign InfoSecurity. I independently built a comprehensive OT testbed and used it as a training platform, which ultimately enabled us to field three teams for CISS 2024—with our primary team securing second place in the competition.

I am incredibly proud of my teammates and deeply grateful to Warren Chong for his unwavering support and contributions to the training sessions, as well as Achmad Zaenuri Dahlan Putra for his invaluable efforts in the CTF.
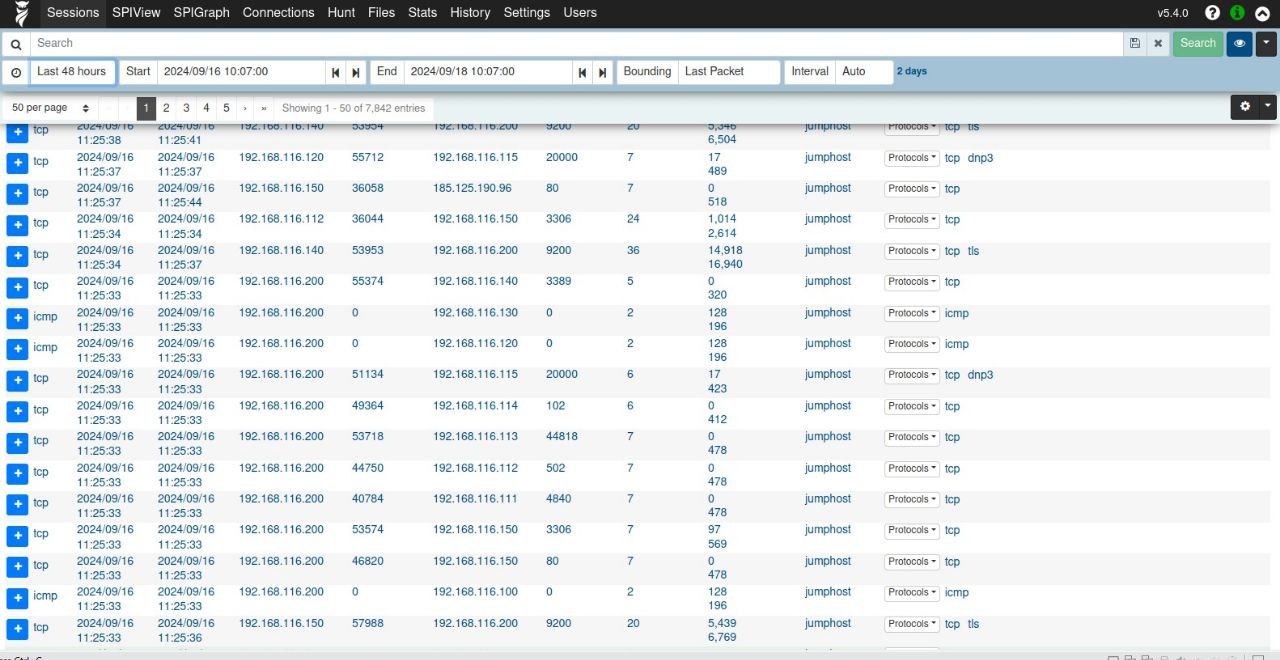
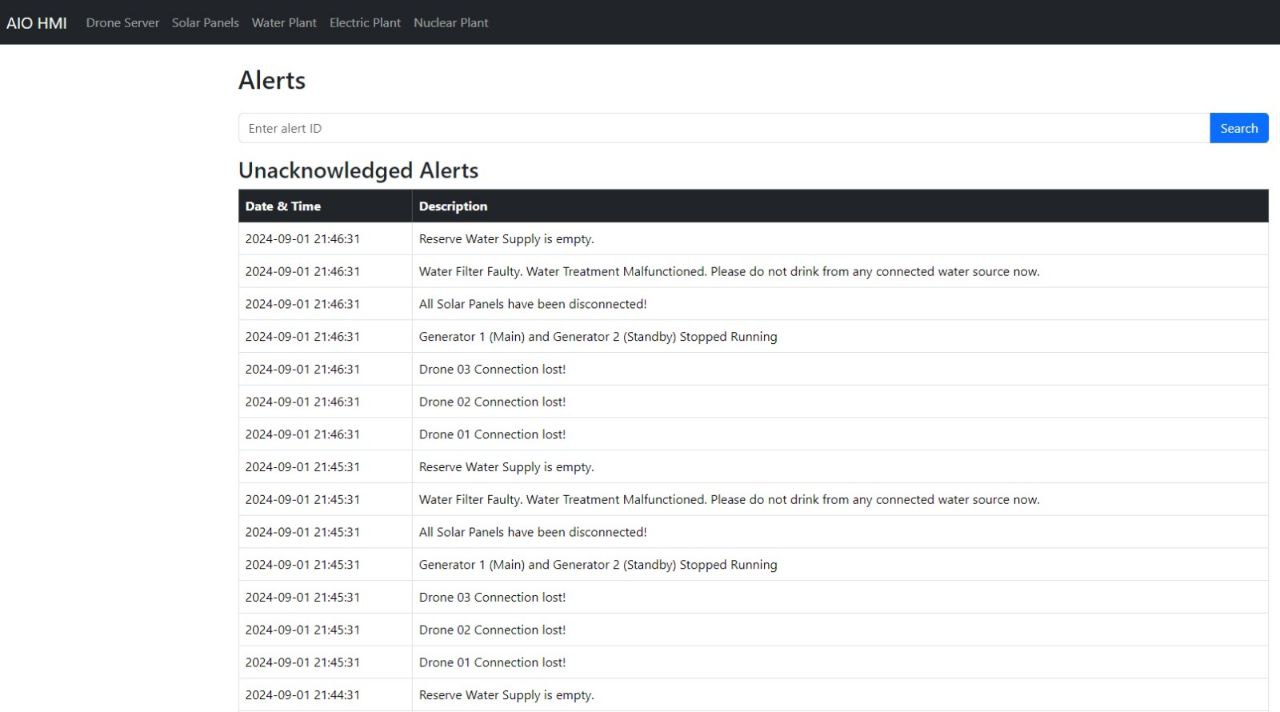
My testbed was designed around a storyline involving a Critical Information Infrastructure (CII) in Singapore, where we simulated threat actor tactics to maximize impact. While the testbed had a strong emphasis on red teaming and OT exploitation, I also integrated multiple SIEM solutions to facilitate blue team training—including traffic analysis, incident response, and threat hunting.
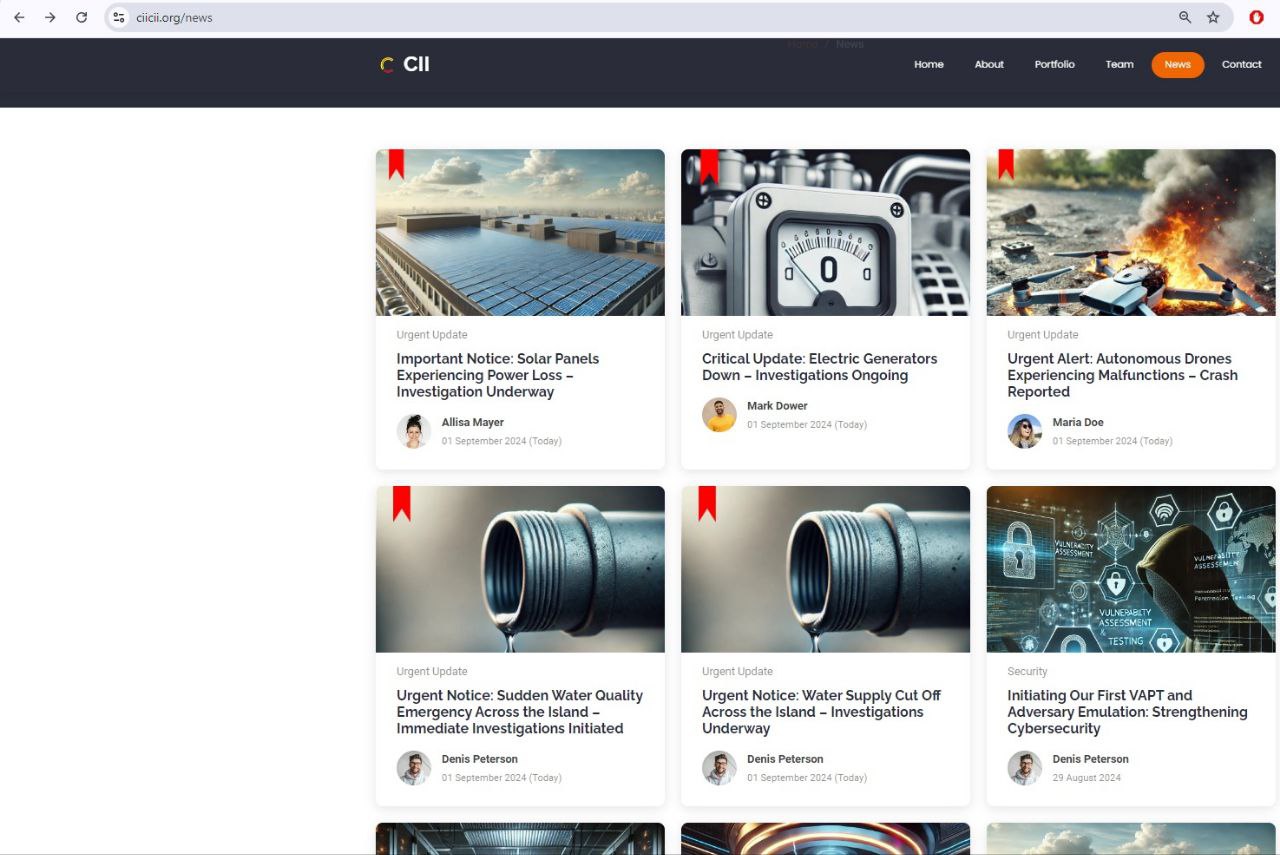
This experience significantly deepened my expertise in OT security, and following CISS 2024, I repurposed the testbed from a training platform to a honeypot to further conduct research and development on the evolving OT threat landscape.